What is the problem?
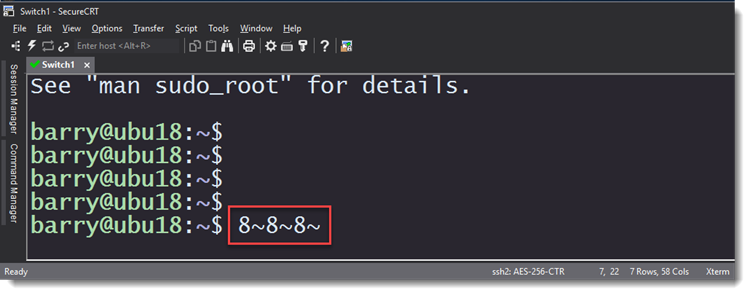
You're using SecureCRT to connect to an HP Aruba network device (or similar) and you have logging enabled. You can see the lines of information that you type in the terminal screen, but those lines are not included in the log file.
Why might this be happening?
In order to eliminate superfluous data from appearing in the log file (like when you mistype a command and have to backspace to correct it), SecureCRT writes data to the log file only when the end of the current line has been reached — in other words, when a CR or LF character is received. Once a CR or an LF character is received, SecureCRT takes the visible text on the current line and writes it to the log file.
Some remote hosts, such as HP Procurve and Aruba switches, don’t follow basic terminal norms in which a "line" is terminated with a CR or LF. When you press Enter to submit a command when connected to such devices, the device does not send SecureCRT any line termination character (a CR or an LF); rather, it sends SecureCRT a sequence of cursor movement codes that cannot be interpreted in a general case as being an "end of line marker". Since there is no CR or LF character received for that line on which a command has been typed — and because the cursor has now been moved to another line — the line with the command won't get logged by SecureCRT.
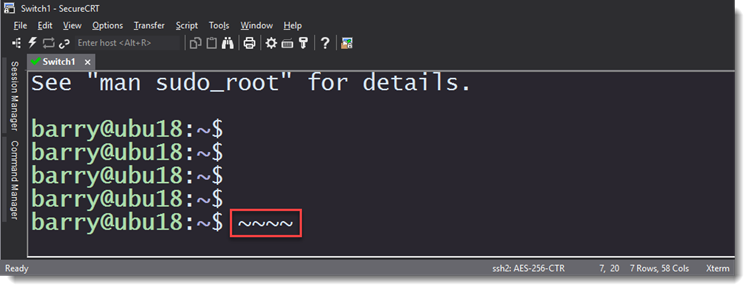
This is an image of the raw log of all of the escape sequences that were sent to SecureCRT by a particular Aruba device after Enter was pressed to complete a command:

A raw log captures ALL characters received from a connected device. You can see that the device doesn't send any CR or LF when a command is echoed back to SecureCRT.
You can also see that the raw log file is unreadable because of the extraneous escape sequences that these devices send whenever any character is typed into the terminal.
What’s the solution? In what SecureCRT version is the solution available?
A new INI-file-only session option called Log Screen was added as of SecureCRT version 8.7. This option allows all data displayed in the terminal to be logged at the time it appears on screen, as opposed to when a CR or LF is received by SecureCRT.
From within a script
When logging inside script code, this is how the option can be enabled:
Python:
crt.Session.Config.SetOption("Log Screen", True)
VBScript: (Windows only)
crt.Session.Config.SetOption "Log Screen", True
Using a button to change the current session's Log Screen option
If you want, you can map a button to a script that enables this option on a per-session basis. Just save the line of Python code shown above to a file named SetLogScreen.py (if you copied the Python code) or SetLogScreen.vbs (if you copied the VBScript code) on your system and map a button to run the script (see the SecureCRT's Button Bar video on our YouTube channel).
When you click the button, the session associated with the active tab will have its Log Screen option enabled.
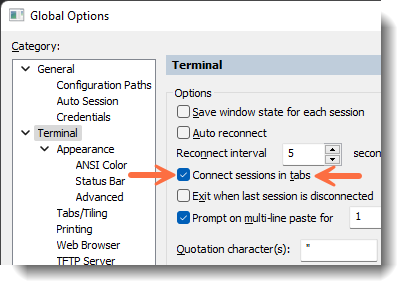
Changing the option manually
If, instead, you want to manually change this setting, navigate to the .ini file for that particular session (session .ini files are found in the Config\Sessions folder on your machine, and the configuration folder path can be seen under the General / Configuration Paths category of Global Options). Edit the .ini file and make the change illustrated below:
change
D:"Log Screen"=00000000
to
D:"Log Screen"=00000001
If there’s no D:"Log Screen" line in your .ini file, the first thing you should ensure is that you're running SecureCRT version 8.7 or newer. If so, then you can simply add the D:"Log Screen"=00000001 line to the end of your session's .ini file.
Note: You should always close all instances of SecureCRT that are running before you edit a session's .ini file.
What caveats are there?
This Log Screen option will log everything that is sent to SecureCRT’s terminal screen. This includes redraws that are caused by backspaces or tab completions, which means that generally, the log file is going to show some interesting things. For example, if you used tab completion and backspace to correct some errors a couple times while typing in the following command:
show ip route connected
…in the log file you might see something like this:
Aruba-1# shiAruba-1# shoAruba-1# show ip royAruba-1# show ip rouAruba-1# show ip route connAruba-1# show ip route connected
For each backspace or tab completion, the device actually re-draws the entire line; and these re-draw occurrences will show up in the log file because SecureCRT is now logging every character that has been displayed on the screen.