As Internet access becomes increasingly inexpensive and available, it has become a viable replacement for traditional couriers, telephone, and fax, as well as remote dial-up access to a company's internal computer resources.
One of the biggest challenges in using the Internet to replace more traditional communications is security. In the past, companies have maintained their own modem bank dial-up access to company resources so that critical data wasn't being transmitted over the public network. Modem banks are expensive to maintain and don't scale well. In a large company, long distance charges for road warriors alone can make this an expensive solution.
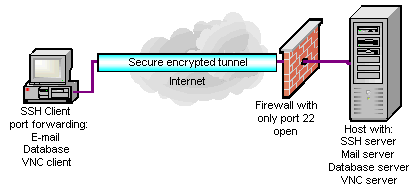
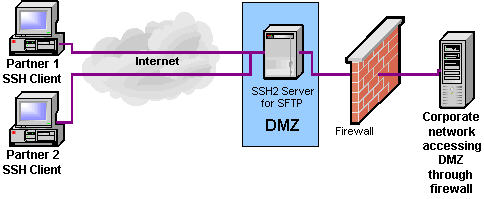
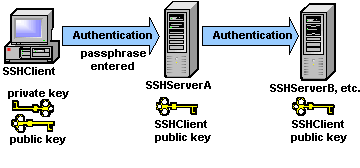
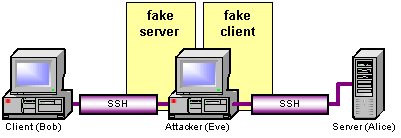
Secure Shell is a protocol that provides authentication, encryption and data integrity to secure network communications. Implementations of Secure Shell offer the following capabilities: a secure command-shell, secure file transfer, and remote access to a variety of TCP/IP applications via a secure tunnel. Secure Shell client and server applications are widely available for most popular operating systems. Secure Shell offers a good solution for the problem of securing data sent over a public network.